
If organizations want to have any chance of protecting their data from unauthorized access in 2025 and beyond, there is no way around Identity Governance & Administration. But conventional IGA solutions are the wrong option for most businesses.
For companies trying to keep their data secure while maintaining a competitive edge, the stakes could not be higher. Faced with an onslaught of identity-based attacks, they need a way to efficiently manage their increasingly complex IT environments while ensuring that only the right people have access to right resources.
Identity Governance & Administration (IGA) offers just that: effective access control and a way to automate essential governance tasks.
- Lifecycle management provides each user with the exact privileges they need for their current role while eliminating the hassle of manual on/offboarding.
- Self-service requests and approvals allow you to delegate access decisions and free up your helpdesk – while always staying in the loop.
- Separation of duties prevents users from holding conflicting privileges, even across different IT systems.
- Access reviews and in-depth reporting tools ensure that user access remains appropriate, even as roles and responsibilities change.
Once they are fully operational, IGA solutions improve your security posture, lower your IT workload and provide the visibility you need to maintain compliance with a wide range of regulations and frameworks.
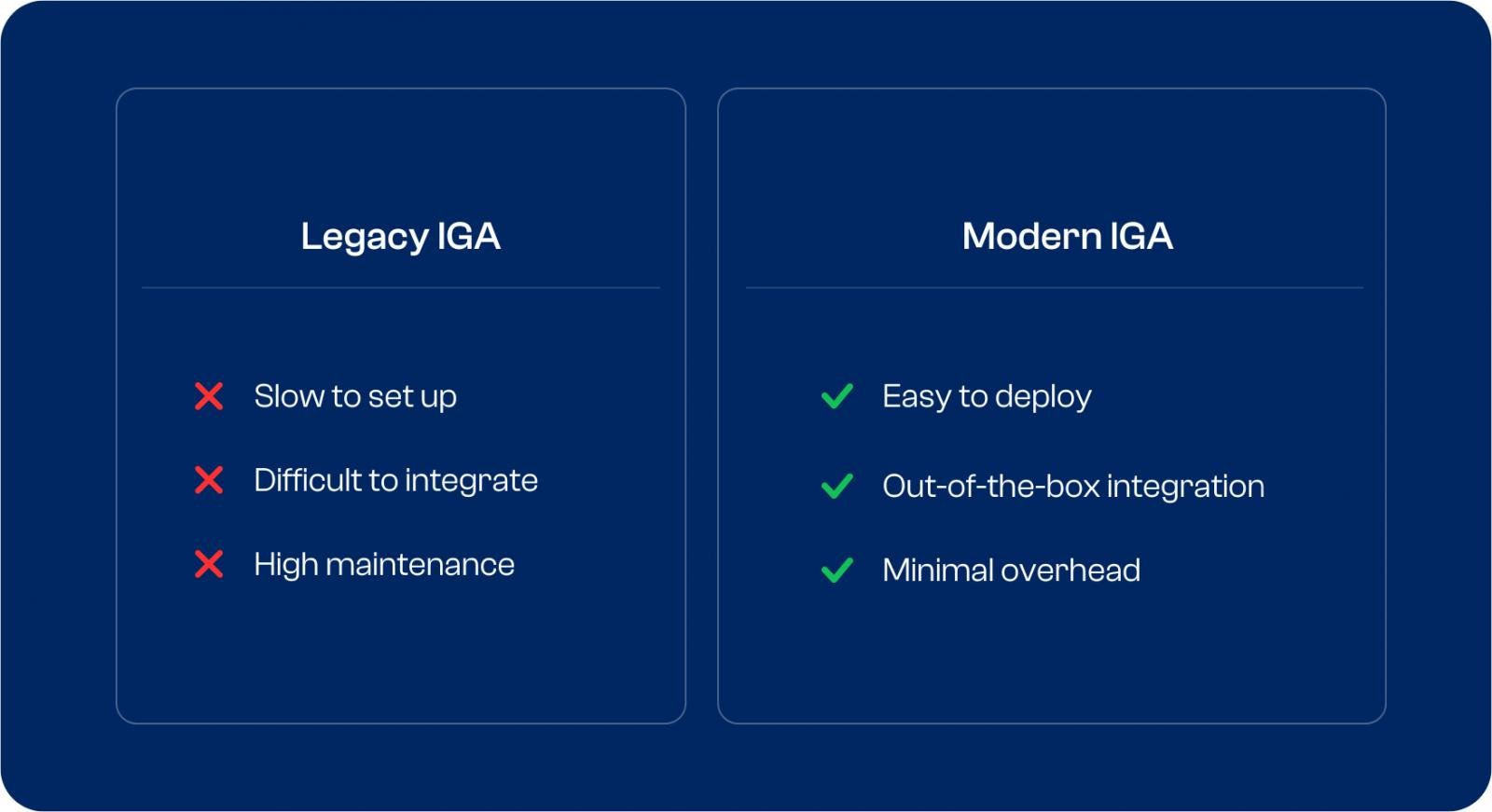
There is one problem, however: Getting IGA ready takes a lot longer than you expect. Unlike their modern counterparts, conventional IGA solutions are difficult to set up and use – a major roadblock on the path to streamlined governance.
Legacy IGA: What a typical deployment looks like
In order to govern access across different systems, an IGA solution must first be connected to the different apps and platforms that make up your IT environment. This is not as easy as it sounds. Legacy solutions generally ship with plugins that can act as basic connectors.
The real integrations, however, are built from the ground up during the setup phase – a process that involves a lot of planning, meetings and custom code.
In theory, this approach is intended to make Legacy IGA infinitely customizable, allowing the final integrations to be tailored to your exact needs and specifications while modeling any business process, no matte…
